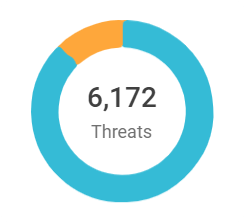
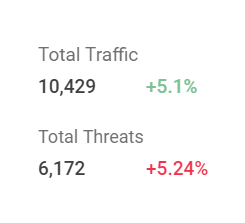
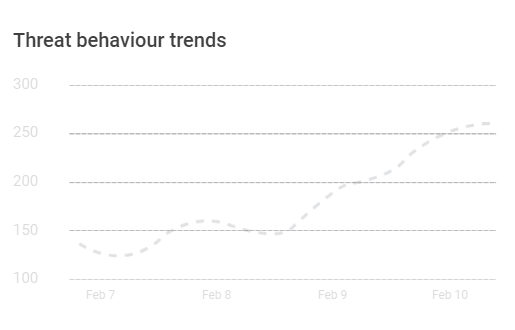
Security Center
We have harnessed the unparalleled capabilities of sso.id Customer Identity Cloud to forge an innovative pathway toward a unified perspective on authentication events, potential security incidents, and the efficacy of our threat response.
Try Now